According to recent Cisco projections, the Internet of Things (IoT) is a $14 trillion revenue opportunity that Gartner estimates will contain 25 billion connected things by 2020. It is increasingly recognized that the full potential of connected devices and systems can only be achieved when these connected things are associated with individual identities. According to IoT Evolution World, products and services connected through individual identities can increase value for customers by providing highly personal experiences and allowing enterprises to not only monitor their product’s performance, but also better understand how customers use them.
Of course, with an increasing number of products and services connected by identities, there is a growing need for strong identity management providers to ensure these connected systems remain secure.
Four Identity Focused Security Concerns
As you begin to look for an identity and access Management as a Service (IDaaS) provider, there are several key areas of security to be concerned with.
- The connection method used to integrate your existing corporate directory. Transferring both employee and customer user information into a provider’s controller directory can seem risky, so make sure you choose a provider that supports an authentication standard which gives you the most control over authentication and security.
- The storage of data such as corporate groups and users. Keep in mind that most IDaaS solutions do not automatically store user passwords, although this is generally an option. Allowing your IDaaS provider to store user passwords will also be necessary if you plan to take advantage of their Single Sign On (SSO) capabilities. Make sure to consider any and all legal and security implications that might arise.
- The communication between your IDaaS provider and your entire portfolio of SaaS applications. An IDaaS provider will not do you any good if it does not integrate with the other Software as a Service (SaaS) applications your enterprise already uses. Most IDaaS providers support the Security Assertion Markup Language (SAML) standard for authentication and offer password vaulting for those applications that are not configured for SAML.
- The user sign-on process. Look for an IDaaS provider who supports multifactor authentication (MFA) in their sign-on portal. MFA requires authentication beyond a basic password and provides increased security when accessing your systems.
These security concerns become even more important if you are looking for an IDaaS provider that also has SSO and mobility management capabilities.

Okta Identity Management: The Sole leader in Gartner’s IDaaS Magic Quadrant
In June of 2015, Gartner named Okta Identity Management the sole leader in its Magic Quadrant for Identity and Access Management as a Service (IDaaS). Gartner, which also named Okta a Magic Quadrant leader in 2014, specifically highlighted the Okta Identity Platform, which allows developers to support integrations with customers’ applications and workflows. Additionally, the report noted that Okta’s investments in mobility management have paid off, making them one of the leaders in the area with support for functions such as mobile SSO, device access policies, and device PIN reset.
All vendors considered in Gartner’s Magic Quadrant for IDaaS must deliver a predominantly cloud-based service such as identity governance and administration, access including user authentication, single-sign on (SSO), and authorization enforcement, as well as business intelligence monitoring and reporting.
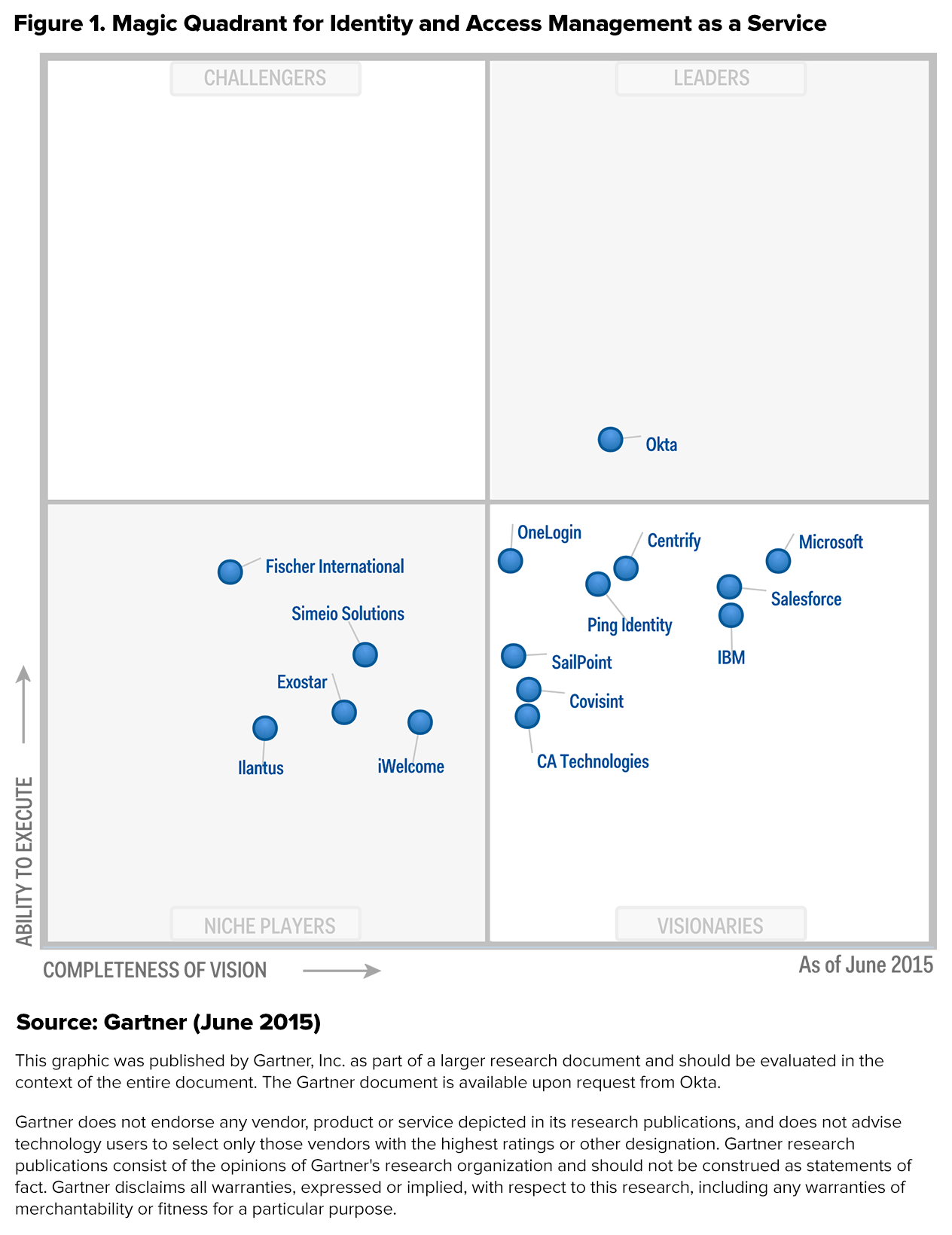
Okta was also featured in Forrester’s second quarter B2E Cloud IAM report as one of the top IDaaS providers because of its large installed base, extensive mobility support, and continuing plans to grow their identity intelligence capabilities.
Is Okta Right for Your Enterprise?
Most recently, Okta was awarded PCMag.com’s Editor’s Choice for IDaaS providers. Okta has long been and remains a leader with key features like multifactor authentication (MFA) and automated Software-as-a-Service (SaaS) application user provisioning. However, what has set Okta apart from the competition and ultimately won it the Editor’s Choice was its ability to integrate with multiple identity providers such as Active Directory (AD), Google Apps, Workday, and more without compromising on data quality.
If you are thinking about Okta as an IDaaS provider for your enterprise, here is a helpful infographic from PCMag.com on the most important areas of Okta’s service that might matter to you most.
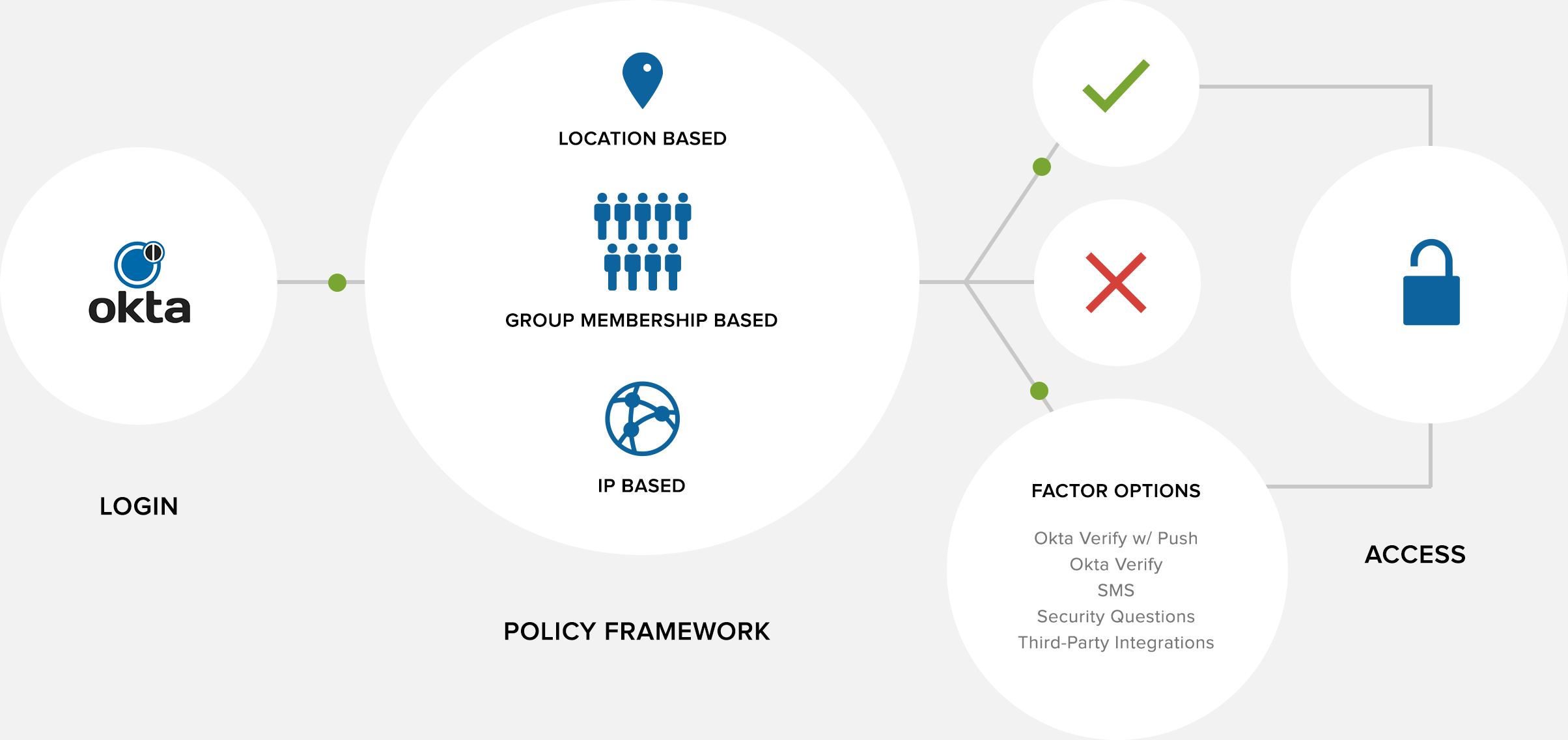
Directory Integration
Larger enterprises might have multiple data sources for identity information, and making these work together can create a certain amount of pain. Okta solves this by supporting several sources of user information which can each be synched with the cloud-based Okta Universal Directory. Probably Okta’s most exciting feature is its ability to configure which data source should be the master source for specific attributes. While the master-level attribute data will normally be stored in another source like AD, Okta has the flexibility to pull this information from that source, “massage the formatting” in their expression engine, and push it into another application or directory. This allows for user identity data to be pulled up from any of the synched data sources, maintaining system security and cutting down on time spent configuring each connected application.
User Provisioning
You can start importing users to your Okta Universal Directory once the AD agent is installed and directory integration settings are configured. Okta uses this import process to gather and validate user account information based on whether the user matches an existing Okta Identity Management account or not. At this time you can also configure import protocols for each category of users, such as which users can be automatically imported and which might require administrator approval.
Like most other IDaaS providers, Okta supports the Security Assertion Markup Language (SAML) standard for SSO authentication to other applications and also offers password vaulting for applications that do not support SAML.
Where Okta really stands apart is its ability to configure a service once and then link to multiple applications within that service (e.g. which functions like Google applications within your Google Account). Okta also offers the option to enable MFA to increase security in multiple forms including Google Authenticator, RSA Secure ID, and Okta’s own Verify mobile application. Finally, all of these user-facing login portals can be completely customized to best serve your enterprise, including even log-in field labels, URLs, and Help files.
Reporting
Although Okta’s reporting engine lacks the customization and scheduling capabilities of competitor OneLogin, it does give you access to log data that is completely searchable and sortable. Most importantly, all of this data is downloadable, allowing you to use and interpret it beyond the limits of Okta’s own reporting tool.
Pacific Timesheet makes it easy to implement IAM/SSO system integration to support SSO and Identity Management Integration with time, work, asset, and field documentation tracking by integrating with Okta Identity Management and any SAML 2.0-based SSO/IAM provider.